Cjdns Mesh Networking
by John Haverlack 2020-06-19
Cjdns1 establishes an encrypted IPv6 mesh network by routing traffic over of common IPv4 networks thus enabling the secure tunneling of IPv6 traffic between any 2 cjdns hosts (Win/Mac/Lnx/Rpi) in the cjdns mesh network. CJDNS IPv6 addresses works for almost any existing IP based service (HTTP/S, SSH, Squid, etc.) Thus nothing special need to be done to configure services on CJDNS mesh networked nodes.
So what is cjdns good for? Cjdns makes it possible to create private mesh networks between hosts on top of underlying Internet networks for secure access to between mesh network nodes regardless of the underlying network topology. This is a powerful capapablity for legitimate purpose but can also constitute a security back door if untrusted nodes are permitted to join.
Network Topology
Before we dive into cjdns we need a little network 101 background to set the context. There are many topological 2 ways that IP3 devices can be connected to route network information between nodes in the network.
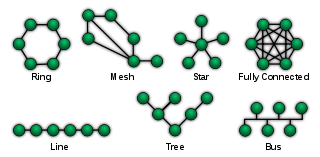 NetworkTopologies.svg4
NetworkTopologies.svg4
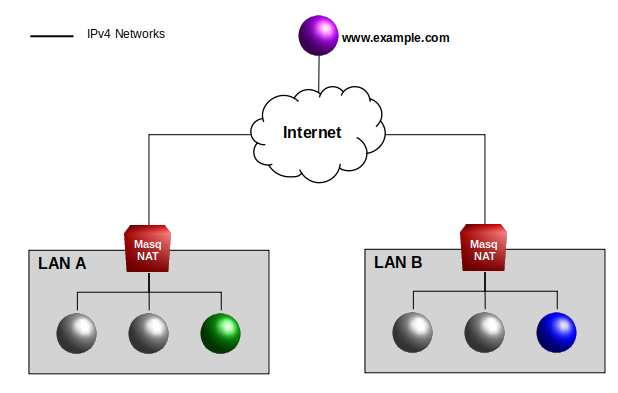
In today's Internet, a Masquerading NAT5 Firewall-Router (Masq-NAT) is commonly used on the boundary between a Local Area Network (LAN) and Wide Area Networks (WAN) (aka. the Internet) to issolate internal LAN traffic from the Internet. Ignoring the many details, generally speaking in the following is true of a Masq-NAT topology:
- IP nodes behind a Masq-NAT LAN boundary can connect to Internet nodes.
- IP nodes behind a Masq-NAT LAN boundary can connect to other nodes in the LAN.
- IP nodes outside of the Masq-NAT LAN boundary cannot connect to nodes inside the LAN.
It is not possible for a node in LAN A to establish an IP socket connection directly with a node in LAN B.
NAT Traversal
Because nodes outside of the Masq-NAT LAN boundary cannot initiate IP socket connections to nodes inside the LAN, Masq-NAT routers provide a significant security boundary blocking malicious traffic from the Internet even without more advance firewall rules. However this also has the consequence that nodes from two different Masq-NAT LANs cannot establish IP socket connections to each other.
To solve this problem and allow host behind Masq-NAT boundaries to talk to each other a few NAT traversal protocols have evovlved. These include STUN8, TURN9, and ICE10 which host servers on the Internet to act as brokers facilitating the establish connection but once a session is established traffic routes directly between the LAN hosts and is not routed through the STUN/TURN/ICE server. NAT traversal is used by many modern applications including Zoom, Skype, Slack, etc. However allowing hosts to perform NAT traversal completely undermines the notion of safety behind a firewall because NAT traversal bypasses those controls. So a malicious application can easily use NAT traversal for nefarious purposes.
Cjdns does something similar but distincly differnt from commong NAT traversal protocols.
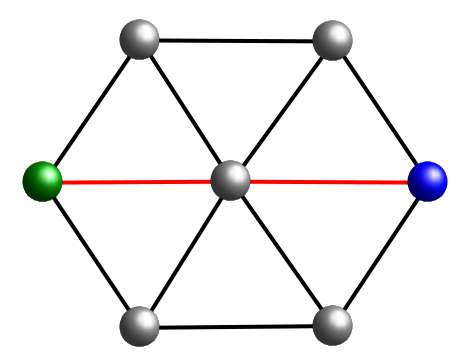
Mesh Networks
In mesh networks11 nodes connected to other nodes can route traffic through the mesh from any node to any other node in the continguous mesh network.
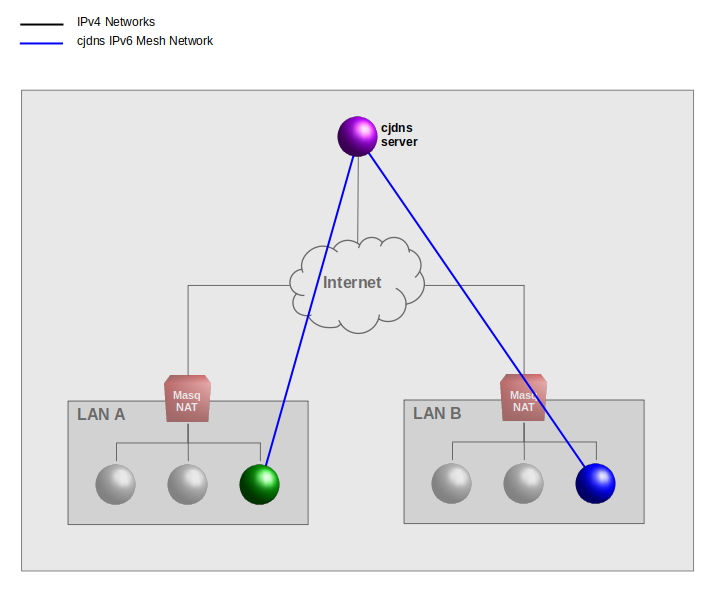
Cjdns Mesh Networks
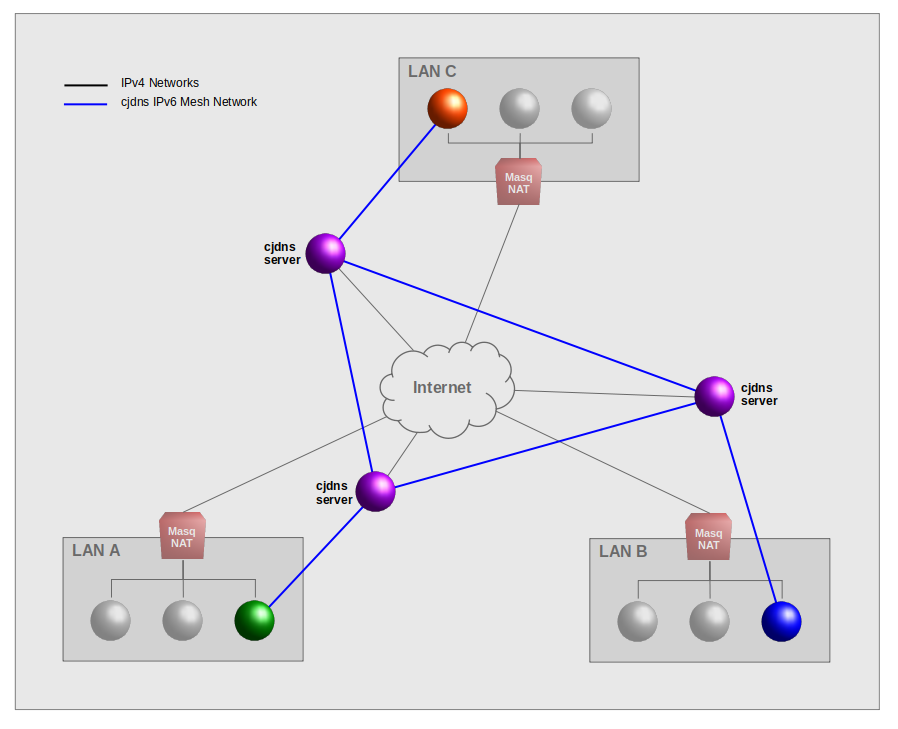
Consider 2 nodes in LAN A and 1 node in LAN B that each connect to a cjdns server on the Internet (purple connections). Cjdns clients must autenitcate connections to cjdns servers such that only autorized host can join the mesh network. Only one cjdns server is needed to establish the mesh network. Having multiple cjdns servers increases the resiliency of the mesh network.
Once a client has authenticated to atleast on cjdsn server in the mesh network it can now establish IPv6 socket connedtions to any other host in the network (red connections). Thus a cjdns host in LAN A can connect directly to a host in LAN B by the cjdsn IPv6 address. And viceversa.
Cjdsn create a separate encrypted IPv6 mesh network topology between authenticated member hosts, on top of the underlygin IPv4 networks using designated Internet "cjdns servers". However the distinction between client and server is a thin line as any client can be a server to other clients.
Caveats
Security Concerns
Because any cjdns client can also be servers, if cjdns client are not strictly administered, it is easy for unknown host to join the mesh networks. If each and every mesh network member can be tightly managed as trusted peers then a cjdns mesh network does not represent a security risk. However an open membership mesh network would represent a significan security risk to any Local Area Networks.
Continued Supported
Cjdns has not
Yggdrasil7
Cjdns Installation
Linux
Raspberry Pi
OS X
Windows
http://www.santacruzmesh.net/installer.html
CJDNS is dead, long live Yggdrasil